19.3.1 The scalability of local and remote attacks
Why do we care whether an attack is local or remote? The answer is scalability – an attack characteristic closely related to the economic concept of marginal cost. In economics, the marginal cost of goods refers to the additional cost incurred by producing one more unit of those goods. Similarly, the scalability of an attack refers to the additional cost, time, or effort Mallory has to invest to attack one more system or user. If the attack’s marginal cost is low, its scalability is high.
Take, for instance, modern cars. One way to attack a vehicle’s safety-relevant functionality – albeit not related to information security – is to cut its brake line carrying brake fluid under pressure to activate the brakes. Although somewhat hypothetical, this example is quite illustrative.
In principle, the attack would work. However, it would require Mallory to visit the geographic location of every car she wants to attack. If Mallory were to attack 10,000 vehicles, assuming a 15-minute average attack time per vehicle and 10 hours a day where Mallory can engage gives:
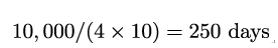
Attacking 100,000 vehicles, therefore, would require 2,500 days or more than 6.5 years, not to mention the financial attack cost. Clearly, such an attack does not scale in practice.
In comparison, assume Mallory knows a zero-day vulnerability that – similar to the famous Jeep hack by Miller and Valasek [120] – can be used to disturb one or more safety-critical Electronic Control Units (ECUs). If Mallory knows the IP addresses of vulnerable vehicles – an assumption we must make following Kerckhoff’s principle from Chapter 3, A Secret to Share – she can use an automated script to attack 100,000 cars within a few hours.
Moreover, in contrast to cutting the brake line, Mallory doesn’t even need to know how the 0-day vulnerability works; she only needs access to the exploit code. Obviously, such a remote attack is highly scalable and, therefore, a much more serious concern in practice.
19.4 Interactive versus non-interactive attacks
In an interactive or online attack, Mallory must maintain a connection to and actively interact with her attack target Alice over the entire duration of the attack.
Figure 19.7 illustrates the working principle of an interactive attack. To carry out the attack, Mallory sends consecutive requests to Alice and processes Alice’s responses until the attack succeeds (or Mallory runs out of computational resources or time).
As an example, assume that Alice runs an SSH server configured to accept a username and a password at the login prompt. In that case, Mallory’s attempt to guess that username and password is an interactive attack. The only way Mallory can check whether her guess is correct is by actually entering the guess into Alice’s login prompt and, subsequently – maybe with the help of a script, checking whether the login attempt was successful or not. Hence, Mallory must actively interact with Alice for every new guess.
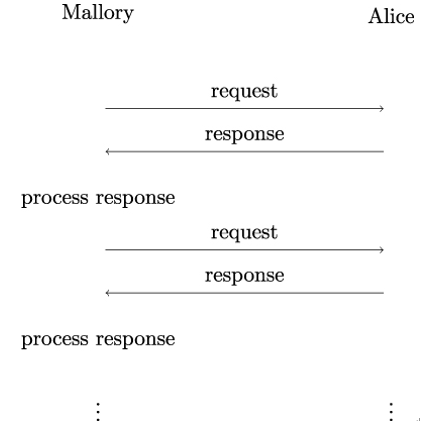
Figure 19.7: Working principle of an interactive attack
In contrast, in a non-interactive or offline attack, Mallory is able to do the computations offline, without having to interact with Alice. In addition, a non-interactive attack is verifiable in the following ways:
- Mallory is able to confirm whether the attack succeeded or not before interacting with Alice
- Mallory can recover a long-term secret using offline computation subsequent to an interaction with Alice
Figure 19.8 illustrates the working principle of a non-interactive attack. In this example, Mallory first interacts with Alice and receives Alice’s response. Mallory then goes on to process the response offline, without interacting with Alice. After she succeeds (or runs out of computational resources or time), Mallory exploits the results to mount an attack.
A non-interactive attack can be thought of as being composed of two phases. During the initial online phase, Mallory acquires the required information. Then, during the offline phase, Mallory uses that information to carry out computations to break Alice’s security.
As an example, assume that Mallory obtains a copy of the password file from Alice’s machine. The password file typically contains hashes rather than plaintext passwords, so Mallory cannot exploit this information directly. However, she can use all the hardware at her disposal to compute hashes for all words from a large dictionary. To perform these computations, Mallory does not need to interact with Alice. Moreover, if Mallory finds a hash value identical to one of those stored in Alice’s password file, she knows that the password guess is correct with overwhelming probability. In other words, she can verify that the attack was successful before (again) interacting with Alice.
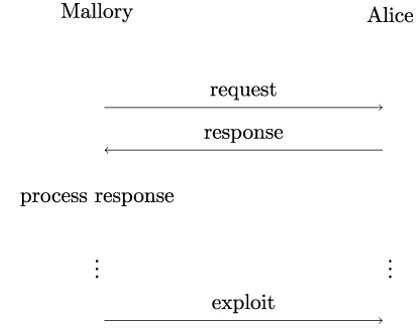
Figure 19.8: Working principle of a non-interactive attack
In general, a non-interactive attack is more dangerous than an interactive attack. Why? Because in an interactive attack, Mallory is constrained by network capabilities such as bandwidth and latency. In the preceding example, every username and password must be transmitted to Alice, and Alice’s response must be sent back to Mallory over the network. So, the network’s speed (and how fast Alice processes the login attempt) limits how many combinations Mallory can test in a given time.
More importantly, because Mallory needs to test a large number of username-password pairs, it is easy for Alice to detect the attack. In fact, Alice can easily prevent the attack, for example, by limiting the number of login attempts before locking the account for a predefined period of time.
If Mallory, on the other hand, can mount a non-interactive attack, she can use all the computing power she can afford – checking tens of thousands of username-password combinations per second – without Alice ever being able to notice that.
Leave a Reply