20.1.3 The Downgrade Dance
Originally, the Downgrade Dance is a mechanism to negotiate a commonly supported TLS version for client and servers during the TLS handshake. However, up to and including TLS version 1.2, the messages of the negotiation process are not authenticated, so that an active attacker acting as a man-in-the-middle can misuse this mechanism and enforce a lower protocol version upon client Bob and server Alice.
Figure 20.2 shows how the attack works: Mallory simply suppresses all ClientHello messages from Bob and answers them in the name of Alice by a FatalHandshakeError, until Bob sends a ClientHello containing a TLS version number that suits Mallory. Mallory now forwards the ClientHello from Bob to Alice:
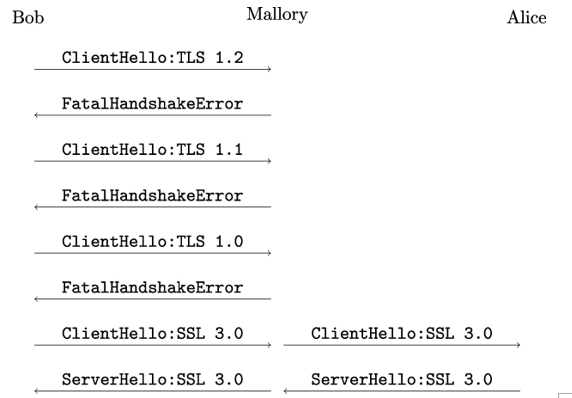
Figure 20.2: The Downgrade Dance. Although Bob and Alice both support TLS version 1.2, they are forced to negotiate SSL version 3.0 by Mallory
Provided Alice accepts the low protocol version proposed by Bob, the handshake continues normally after the Downgrade Dance. Note that Alice and Bob cannot detect the early manipulations by Mallory because the Handshake messages are only protected by the final finished message if the Handshake has been successfully completed.
Clearly, simply downgrading the protocol version is not a goal for Mallory in itself. Rather, by downgrading the protocol version, Mallory can take advantage of vulnerabilities and weaker cryptographic algorithms from earlier protocol versions. The SLOTH (see Section 20.3, SLOTH, in this chapter) and POODLE (see Section 21.2, POODLE, in Chapter 21, Attacks on the TLS Record Protocol) attacks are prime examples of this tactic.
Note that with TLS 1.3, the Downgrade Dance will not happen anymore: a TLS 1.3 server Alice that is asked by the client to negotiate a lower protocol version must include the seven bytes 44 4F 57 4E 47 52 44 (ASCII code for DOWNGRD) as the last bytes of the ServerRandom number in their ServerHello message.
These bytes are authenticated (i.e., signed by Alice) and cannot be changed by Mallory. They indicate to the client that the server supports version 1.3 and downgrading is going on. If the negotiated TLS version is lower than the version supported by the client, something is obviously wrong. Moreover, SSL 3.0 must not be negotiated by TLS servers later than version 1.1 (see [16]) because of its many security problems.
In the next sections we will see how these downgrade attack templates can be turned into real-life attacks.
Leave a Reply