19.5.5 Reflection attacks
A reflection attack is a specific type of an interleaving attack where Mallory sends data she received from Bob in one protocol run back to him in another protocol run. Essentially, Mallory reflects the data back to Bob – hence the name of the attack – in an attempt to trick Bob into providing the answer to his own challenge.
Reflection attacks typically target challenge-response entity authentication protocols. Let’s look at a specific example to understand how these attacks work.Figure 19.14 shows an example challenge-response protocol from [7]. To authenticate Bob, Alice generates a nonce N and sends it to Bob (in clear text). Upon receiving N, Bob encrypts it with the secret key k he shares with Alice and replies with the message ek(N).
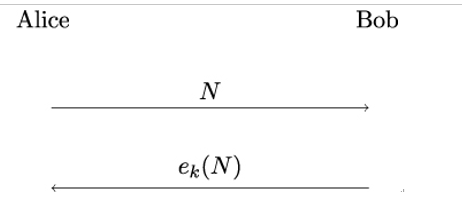
Figure 19.14: Example of a simple challenge-response protocol
Finally, Alice decrypts Bob’s message and compares the decrypted nonce with the nonce she sent to Bob. If the two match, Alice knows that the communicating party claiming to be Bob knows the shared secret key k and, therefore, must be Bob.
The protocol can also be initiated by Bob. In that case, Bob generates the nonce and sends it to Alice so she can respond with the encrypted nonce. Bob then verifies Alice’s response as a means of verifying her identity.
While the protocol might seem robust at first glance, it is vulnerable to the reflection attack illustrated in Figure 19.15:

Figure 19.15: Working principle of a reflection attack
Here, Mallory wants to impersonate Bob. After receiving the nonce N from Alice, Mallory creates a second protocol run – messages denoted by (2) – while pretending to be Bob.
However, instead of sending Alice a new nonce, Mallory simply reflects N back to Alice, thereby tricking Alice into providing the response ek(N) to her own challenge. Mallory then drops the second protocol run and sends Alice the correct response ek(N) in the first protocol run.
One way to prevent a reflection attack is to include the names of the authenticating parties in the protocol’s messages. If Alice’s challenge was (A,N) instead of just N, Mallory would not be able to reflect that challenge back to Alice without Alice detecting it. This also explains why it is desirable to have names in protocol messages, authenticate all messages (including the challenge), or use different keys for transmitted and received messages.
We now turn to generic attacks on cryptographic primitives. Mostly, we will discuss the attacks on a conceptual level, as they apply to all encryption or hash algorithms irrespective of their concrete incarnation.
Leave a Reply