19.6.4 Known-plaintext attack
In a known-plaintext attack, Eve has access to plaintext-ciphertext pairs, that is, to the ciphertext and the corresponding plaintext. Eve’s goal is to recover the key used to encrypt the plaintexts.
The known-plaintext attack has its roots in World War II cryptanalysis. British cryptanalysts at Bletchley Park who broke the German Enigma encryption system used a technique based on so-called cribs. A crib was a plain language passage believed to occur in an encrypted message.
For example, the daily weather report transmitted by the German military contained the word Wetter (German for weather) at the same location in every such message because of style guidelines of military reports. Using cribs, the cryptanalysts were able to test key hypotheses – effectively performing an exhaustive key search – until the correct key for that day was found.
19.6.5 Chosen-plaintext attack
A chosen-plaintext attack resembles the known-plaintext attack, but with a fundamental difference that Eve is able to obtain ciphertexts for any plaintexts of her choice. Conceptually, Eve is said to have access to an encryption oracle we introduced in Chapter 15, Authenticated Encryption. After querying the encryption oracle, Eve’s goal is to recover the secret key.
19.6.6 Padding oracle attacks
Padding oracle attacks exploit the padding validation of encrypted messages – typically in CBC mode decryption – and are a well-known practical example of a chosen-plaintext attack. A typical CBC implementation decrypts all ciphertext blocks, verifies that the padding is correct, removes the padding, and returns the plaintext of the encrypted message. A popular padding is the so-called PKCS#7 padding defined in RFC 5652 where the value of each added byte is the number of bytes that are added:
01
02 02
03 03 03
04 04 04 04
05 05 05 05 05
06 06 06 06 06 06
…
Eve exploits the regularity in PKCS#7 padding by crafting specific ciphertexts and submitting them, for instance, to a web server. If that server is vulnerable to padding oracle attacks, it will return an error message indicating invalid padding. This information effectively turns the server into a padding oracle (hence the name of the attack).
But how does the attack work in detail? Recall that the CBC mode of operation works by first setting the initial ciphertext block c0 to a randomly chosen initialization vector IV . It then computes every subsequent ciphertext block by XORing the plaintext block with the previous ciphertext block and encrypting the result with the underlying block cipher:
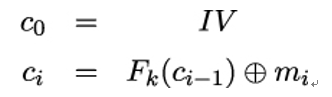
and the corresponding decryption is computed as:
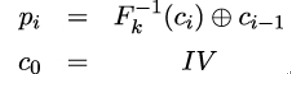
where Fk denotes the encryption and Fk−1 denotes the decryption of a single plaintext or ciphertext block under key k.
Now, suppose Eve has two ciphertext blocks c1,c2 and she wants to recover the corresponding plaintext block p2. Eve changes the last byte of c1 to obtain a manipulated ciphertext c1′ and sends (IV,c1′,c2) to the vulnerable server.
The server, in turn, decrypts the manipulated ciphertext (IV,c1′,c2) and returns an error message if the padding of the decrypted block p2′ is not valid PKCS#7 padding. If, on the other hand, no error message is returned – that is, if p2′’s padding is valid – Eve learns that the last byte of Fk−1(c2) ⊕ c1′ is 0x01. Because Eve knows c1′ and Fk−1(c2) = p2, it is trivial for her to calculate the plaintext block p2 as:
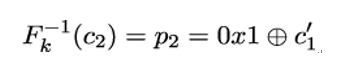
Next, Eve manipulates the last two bytes of c1 until the server returns no error, that is, until the last two bytes are equal to the valid PKCS#7 padding 0x02 0x02. Recall that Eve already knows the value of c1’s last byte to make Fk−1(c2) ⊕ c1′ equal to 0x01 and so can trivially set c1’s last byte to make that value 0x02. Eve, therefore, only needs to guess the value of a single byte – namely, the second-last byte of c1 – which amounts to merely 256 possibilities. She can continue the attack for the remaining bytes of c2 and, as a result, recover the entire p2.
The padding oracle attack was originally discovered by the French cryptographer Serge Vaudeney in 2002. SSL, the predecessor of TLS, and the IPSec protocols were vulnerable to this attack.
Leave a Reply